Kaseya VSA
Patch Management Software
Install, deploy and update software across all endpoints
Patching has never been this easy
Keep software patching up to date to maintain security of your IT infrastructure. Remediate critical software vulnerabilities.
Gain full control over patching including the ability to skip problematic patches by automating the process with scripts.
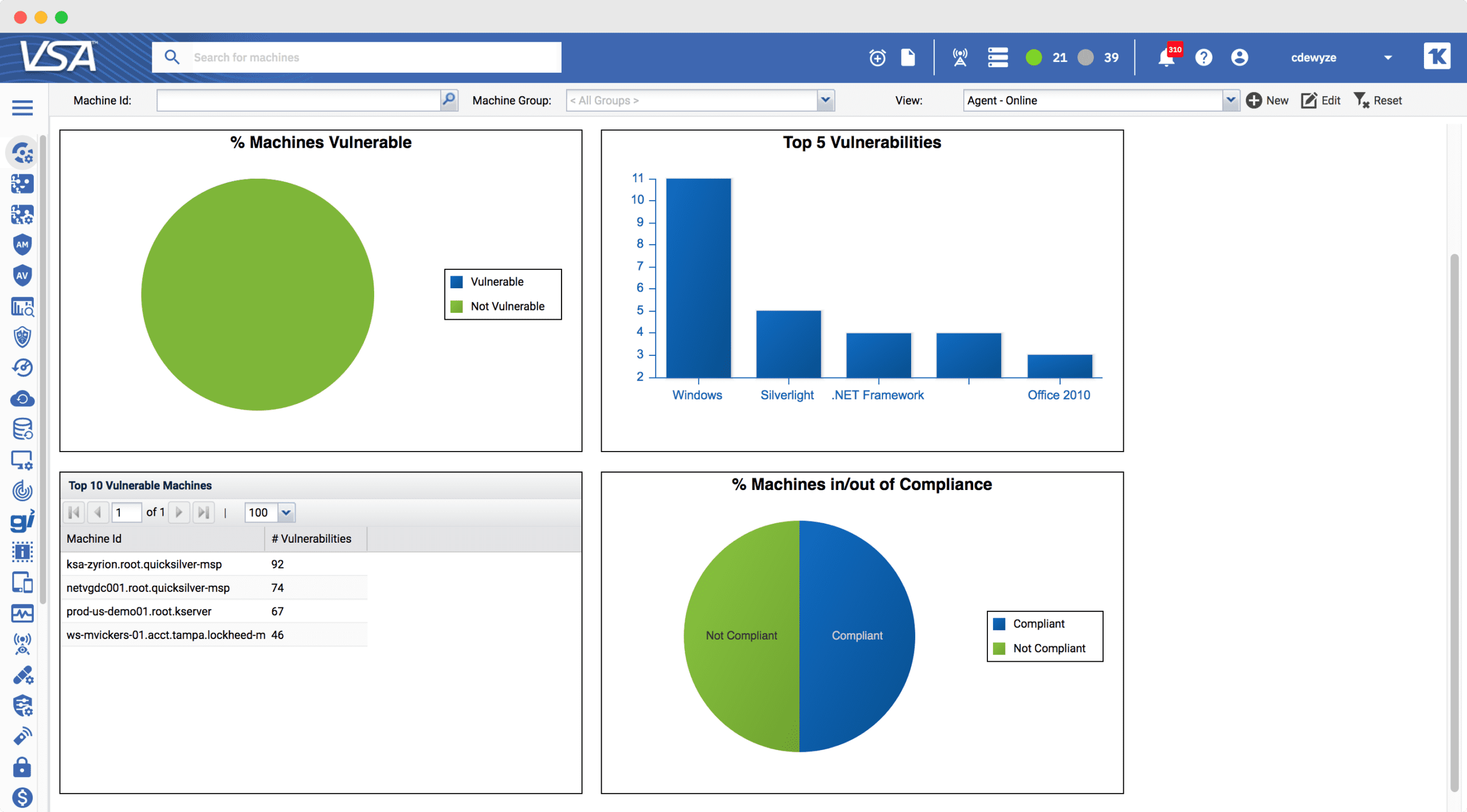
Easily set up patch reports to see compliance across your entire environment and quickly identify the endpoints that need attention across OS and third-party applications.
Gain visibility into vulnerabilities (CVEs) by aggregating the patch status of your IT environment in one dashboard
Remediate Vulnerabilities
Learn how the Software Management module in VSA provides real-time visibility into the patch status of your on-and-off network devices.
Monitor Vulnerabilities
Learn how you can unify software management for Windows, Mac, and third-party applications and apply patches intelligently.
Deploying Applications
Learn how to easily install, uninstall, update, repair, and make many other types of software changes from a single console.
What can Patch Management do for me?
Automate and standardize software maintenance across platforms. Address the complexities of patch deployment with our easy to use policy profiles that allow you to manage patch approvals, scheduling, and installation.
Use the VSA agent endpoint fabric to optimize the delivery of installer packages. VSA eliminates the need for a centralized File Share or LAN Cache.
Schedule a Scan & Analysis of the network on a regular basis so you can automate software updates without disrupting your users.
Blackout Windows enable you to halt processing during a defined period of time.
Allows you to deny a specific patch, KB, or block a specific update to a subset of machines, overriding the default patch classification.
Featured Case Study
Jacobs Engineering Group Leverages Kaseya VSA to Automate IT Management
Jacobs Engineering Group is a world leader in design, engineering, construction and technical services, delivering end-to-end innovative solutions that provide superior value to its clients. One business unit in the company uses Kaseya for IT management. This group mostly works in the aeronautical field with NASA and the Department of Defense.
Travis Graef, Assistant System Administrator, is one of the six people in the organization’s IT Team. His areas of responsibility run the gamut of everyday IT operations tasks.

Download Our Tipsheet
3 Tips to Secure Your Endpoints
Download this Tip Sheet to understand how Kaseya VSA can effectively incorporate patch management and protect your endpoint from vulnerabilities.