All businesses with an online or digital presence, whether large or small, irrespective of industry, are exposed to cyber risk today. To help prepare and protect companies from these cyber risks, the U.S. Government has issued guidance in the form of a framework from the National Institute of Standards and Technology (NIST), called the NIST Cybersecurity Framework.
What Is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a voluntary framework that consists of standards, guidelines and best practices issued by the U.S. Department of Commerce. It is a collaborative effort between the public and private sectors and academia. It was originally targeted at improving cybersecurity for critical infrastructure sectors in the United States. Those key sectors included finance, energy, healthcare and defense. It was also intended to be used by federal agencies as well as state and local governments. Version 1.0 of the NIST CSF was released in February 2014.
The framework has since been revised, with the goal of making it flexible enough to be used by small and large businesses across every industry sector. It also has broader applicability to not just IT but also the IoT— Internet of Things. The latest version of the NIST CSF is version 1.1, which was released in April 2018. The new version included updates on the following:
- Authentication and identity management
- Self-assessing cybersecurity risk
- Managing cybersecurity within the supply chain (including buying guidance for commercial, off-the-shelf products and services)
- Vulnerability disclosure
- Clarifications on the relationship between Implementation Tiers and Profiles
At the time of its release, the Secretary of Commerce, Wilbur Ross, said “The voluntary NIST Cybersecurity Framework should be every company’s first line of defense. Adopting version 1.1 is a must-do for all CEOs.” This still holds true today.
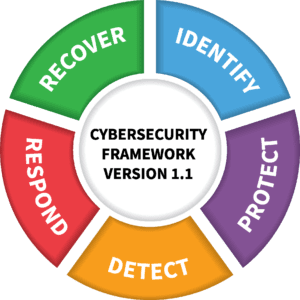
The NIST Cybersecurity Framework consists of three components, which we’ll dive into next.
What Are the Three Components of the NIST Cybersecurity Framework?
The three main components of the framework are:
- Framework Core: A set of desired cybersecurity outcomes organized in a hierarchy and includes five functions of a cybersecurity program – Identify, Protect, Detect, Respond and Recover.
- Implementation Tiers: The Tiers that range from Partial (Tier 1) to Adaptive (Tier 4) provide a qualitative measure of the cybersecurity risk management practice in the organization.
- Profiles: Profiles are an organization’s alignment of its requirements and objectives, risk appetite and resources using the desired outcomes of the Framework Core. These identify opportunities for improving cybersecurity posture by comparing a “Current” Profile with a “Target” Profile.
Let’s take a deeper dive into each of these components and see how they make the framework whole.
Framework Core
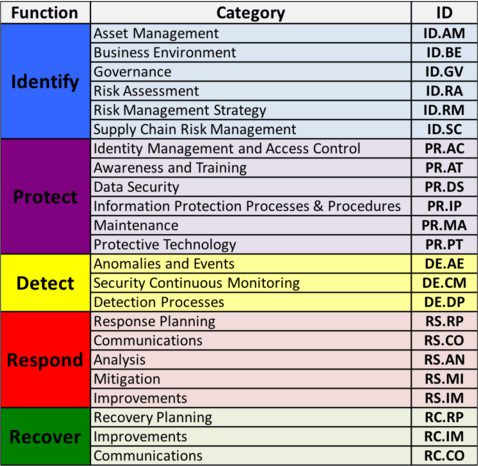
The Framework Core consists of three parts — Functions, Categories and Subcategories, and as mentioned earlier, includes five high-level functions: Identify, Protect, Detect, Respond and Recover. The Categories cover the cybersecurity objectives of an organization and the Subcategories are outcome-driven statements that provide considerations for creating or improving a cybersecurity program. The three components of the Core work in concordance to help an organization manage its risks by organizing information, addressing threats and learning from previous incidents.
The image below depicts the categories in each function.
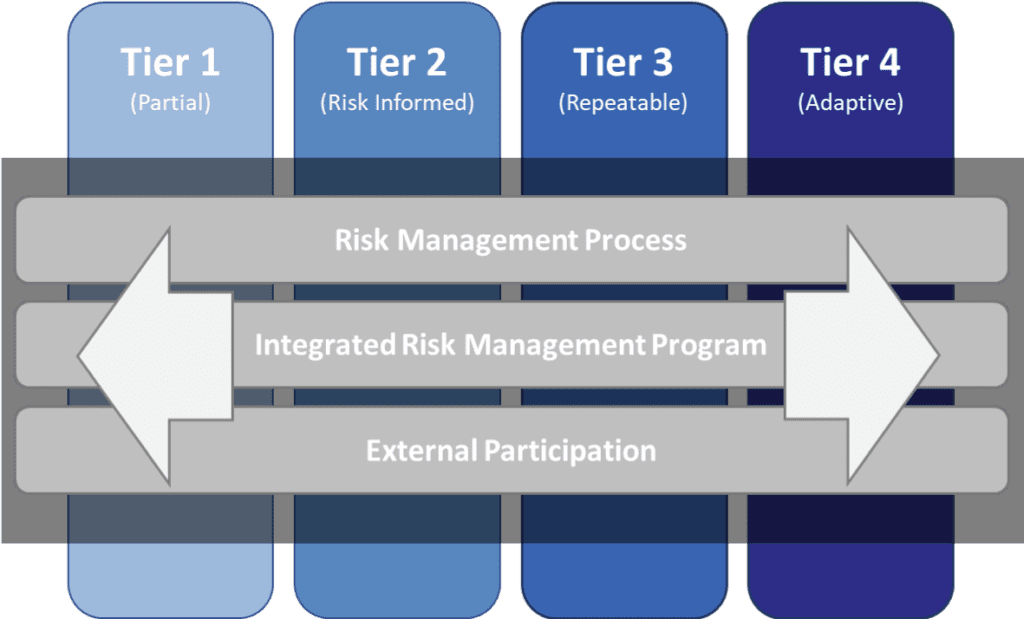
Implementation Tiers
The Implementation Tiers are composed of four tiers – Partial, Risk-Informed, Repeatable and Adaptive. These tiers describe different degrees of sophistication in the measures taken by an organization. The cybersecurity risk processes that collectively indicate a tier are:
- Risk Management Process: The functionality and repeatability of cybersecurity risk management
- Integrated Risk Management Program: The extent to which cybersecurity is considered in broader risk management decisions
- External Participation: The degree to which the organization benefits by sharing or receiving information from outside parties
While tiers do not represent maturity levels, an organization must determine the desired tier and ensure that it meets the goals of the tier by implementing necessary actions and reducing cybersecurity risk.
Profiles
This component of the NIST Cybersecurity Framework enables organizations to establish a roadmap for reducing cybersecurity risk by chalking up their organizational goals, aligning any potential cyber risk to these goals, and following industry standards and best practices to avoid these risks.
An organization can map its cybersecurity requirements, mission objectives and operating methodologies, along with current practices against the subcategories of the Framework Core.
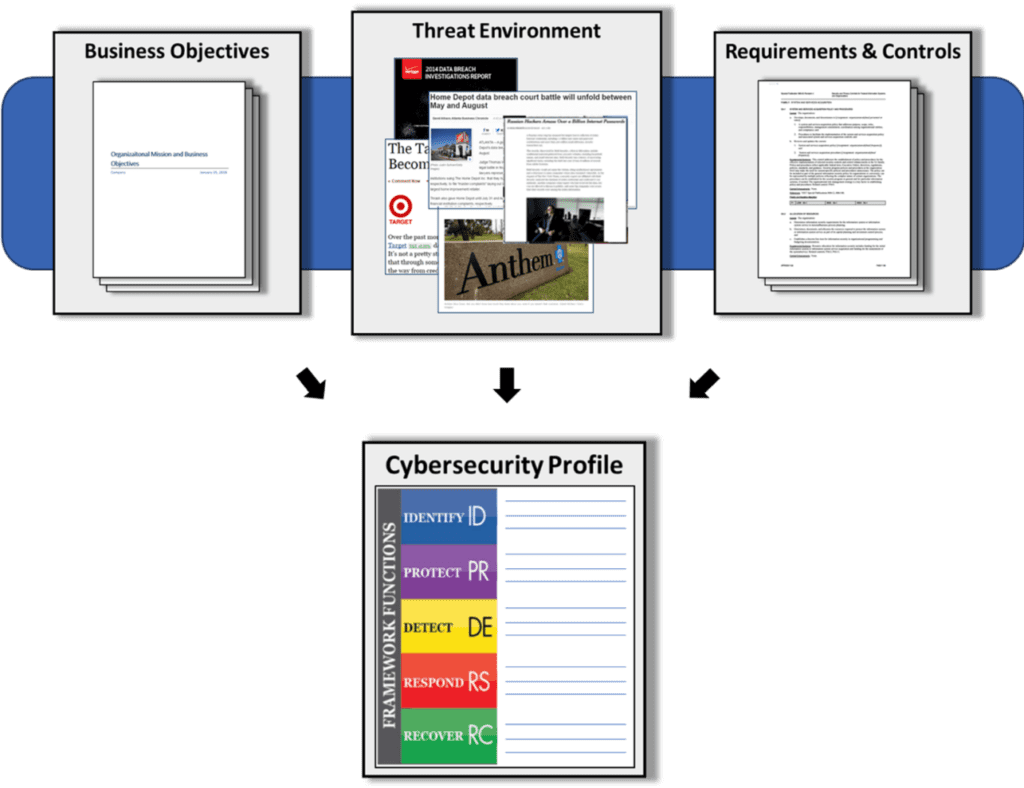
In the above image, when comparing a “Current” Profile with a “Target” Profile, the analysis of the gap between the profiles allows organizations to create a prioritized implementation plan.
Using the NIST Cybersecurity Framework
- Prioritize and Scope – Identify organizational objectives and priorities and identify the IT systems and assets relevant to these objectives. These assets are to be prioritized to be protected at all costs.
- Orient – Identify related systems and assets and regulatory requirements pertaining to these systems. Then identify vulnerabilities of these systems and assets and the threats these could face.
- Create a Current Profile – The Current Profile of your organization should integrate every control found in the NIST Cybersecurity Framework in order to determine which control outcomes are being achieved.
- Conduct a Risk Assessment – Determine the likelihood of cybersecurity events and the impact they could have on your organization.
- Create a Target Profile – Determine where you want your organization to be in terms of cybersecurity posture. Create a target maturity score that incorporates the framework’s Categories and Subcategories assessment and work towards the desired outcomes.
- Determine, Analyze and Prioritize Gaps – Close the gaps between the Current Profile and Target Profile. Create an action plan that involves determining the budgeting, risks and the tasks to be implemented to address the gaps in the Current Profile.
- Implement the Action Plan – Take the steps required to close the gaps as discussed above. Adjust your cybersecurity practices to achieve your Target Profile.
The NIST Cybersecurity Framework, although voluntary, is highly recommended as a way to formulate and manage your cybersecurity programs and processes. The framework:
- Ensures you have robust security policies and standards in place
- Helps your organization enhance its overall security posture against ever-evolving cyber threats
- Provides a process for continuous improvement of your organization’s security practice
Kaseya Compliance Manager enables organizations to demonstrate NIST Cybersecurity Framework compliance with ease. It gives users a high-level overview of how well their organization complies with the framework, identifies gaps in an organization’s protection and compliance, and produces a list of issues users must remediate to ensure compliance.
Users also receive a risk scoring matrix that can be used to prioritize risks and appropriately allocate money and resources to ensure that identified issues are resolved. You can learn more about Kaseya Compliance Manager for NIST Cybersecurity Framework here.
*All images are from the NIST website.
