Cybercriminals never stand still, constantly reinventing their tactics to exploit trust, familiarity and human instinct. INKY continues to observe threat actors weaponizing cloud email platforms and voice‐based social engineering to bypass security controls. A recent example is a phishing campaign that sent hundreds of emails from a compromised SendGrid account linked to OpenAI to issue fraudulent invoices.
An invoice‑themed email, supposedly from OpenAI, arrived from [email protected] via SendGrid. Because the message was sent through a legitimate OpenAI SendGrid account, it passed SPF, DKIM and DMARC checks for openai.com. It claimed that a subscription charge of $763.99 had been confirmed and urged the recipient to call a support number to dispute it. The message contained no malicious links or attachments. Its only call‑to‑action was a phone number. This design allows the scam to slip through URL‑filtering gateways while exploiting the trust users place in well‑known brands and phone conversations.
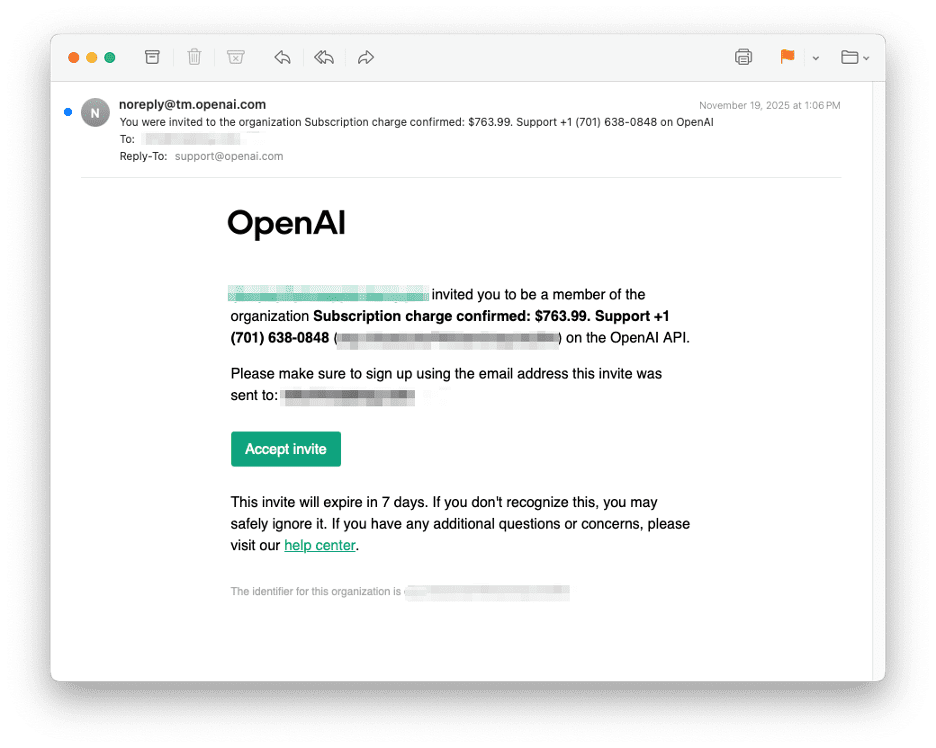
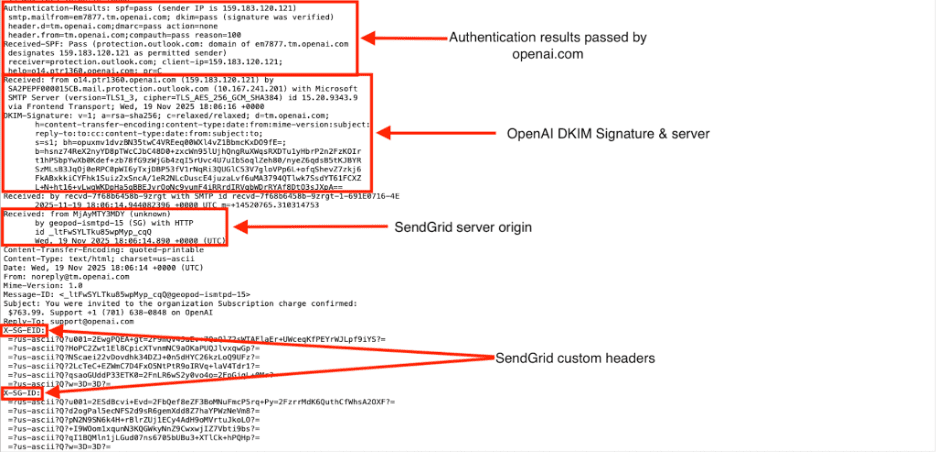
Fig 1: The invoice-themed phishing email Legitimate email delivery platforms have become powerful tools for threat actors seeking to blend in with normal business communications. SendGrid is widely used by businesses to send high‑volume transactional and marketing emails. It offers high deliverability and advanced features, such as click‑tracking and analytics. However, cybercriminals are abusing SendGrid accounts to launch phishing campaigns, impersonating SendGrid itself and other trusted brands. The promise of a 99% delivery rate makes the platform attractive to criminals. A compromised SendGrid account allows them to send spoofed emails that pass SPF/DKIM checks and appear legitimate to recipients. The phishing emails in this campaign were not only spoofing OpenAI’s name – they were sent through a genuine SendGrid account configured on the openai.com domain. The messages passed SPF, DKIM and DMARC checks for openai.com and contained SendGrid‑specific headers, indicating that the sender had authenticated access to OpenAI’s SendGrid tenant. There are several plausible pathways through which criminals could have obtained such access: It is important to emphasise that there is no public confirmation that OpenAI itself was breached. The presence of the openai.com domain in these phishing emails means the attackers had access to some SendGrid credentials tied to OpenAI. Whether this access resulted from stolen credentials, password reuse, a phishing attack against an employee or a compromised third‑party vendor remains unknown. Nevertheless, widespread sale of cracked SendGrid accounts and uncertainty about whether credentials were phished or if SendGrid itself was hacked suggests that the OpenAI invoice scam likely stemmed from account takeover rather than simple spoofing. Organizations using SendGrid should treat this incident as a warning to enforce MFA, rotate API keys regularly and monitor for unusual sending patterns. The malicious email was sent from [email protected] through SendGrid. Header analysis showed multiple hops through Microsoft’s mail infrastructure before reaching the recipient. Key observations include: The combination of SendGrid deliverability, cryptographic alignment and brand impersonation makes such emails difficult for standard email security gateways to block. Fig 2: Email header analysis of the phishing email Callback phishing, also known as telephone‑oriented attack delivery (TOAD), is a scam that begins with a fake invoice or subscription notice. These emails often claim to be charges from well‑known companies and include a phone number to call if the charge is not authorized. Their goal is to make the victim call the number rather than click a link. Once on the phone, the attacker impersonates a customer‑service representative, requesting personal information or instructing the victim to install remote‑support software. Because there are no malicious links or attachments, such messages can bypass traditional email filters. Callback scams rely on urgency: the email urges the recipient to call to cancel a large charge, and a scammer then asks for personal information or remote access. Callback phishing tricks users into calling a provided number. The scammer then uses social engineering to obtain login credentials, financial details or remote access. The method differs from traditional phishing because the conversation moves to a voice call, making it harder for security tools to monitor. Fig 3: Callback phishing message Step‑by‑step chain in the OpenAI invoice case Callback phishing can have severe repercussions. Once remote access is granted, attackers can carry out: To mitigate the risk of SendGrid‑abused callback phishing scams: The OpenAI invoice scam demonstrates how attackers leverage legitimate cloud email services and voice‑based social engineering to bypass security controls. By sending an invoice‑themed email through SendGrid, criminals ensured the message passed SPF/DKIM/DMARC checks and appeared trustworthy. The absence of malicious links allowed the email to evade URL filters, while the urgent call‑to‑action prompted the recipient to contact a scammer who then sought remote access.Abuse of SendGrid infrastructure
SendGrid’s appeal to attackers
Possible compromise of OpenAI’s SendGrid account
Header analysis of the OpenAI invoice email
Attack chain: Callback phishing/vishing
Consequences of callback phishing
Best practices and recommendations
Final thoughts
Callback phishing is part of a broader trend in which attackers weaponize trusted platforms and remote‑support tools. Advanced email security, vigilance, user education and rigorous verification through official channels remain the most effective defenses against this evolving threat.




