Protect Your Business Data, Digital Assets & Users From Cyberthreats
IT Complete’s Security Solutions provide IT professionals with powerful capabilities for defending against cyber threats. Protect your organization with security measures that are integrated into a single platform for maximum efficiency.
Explore Kaseya's Security Solutions
Kaseya’s Security Suite provides threat protection, detection and response. We consolidate your security services for greater efficiency, easy access, control and reliability – while accelerating productivity with intelligent integrations for optimal tool usage and reducing costs up to 30%.
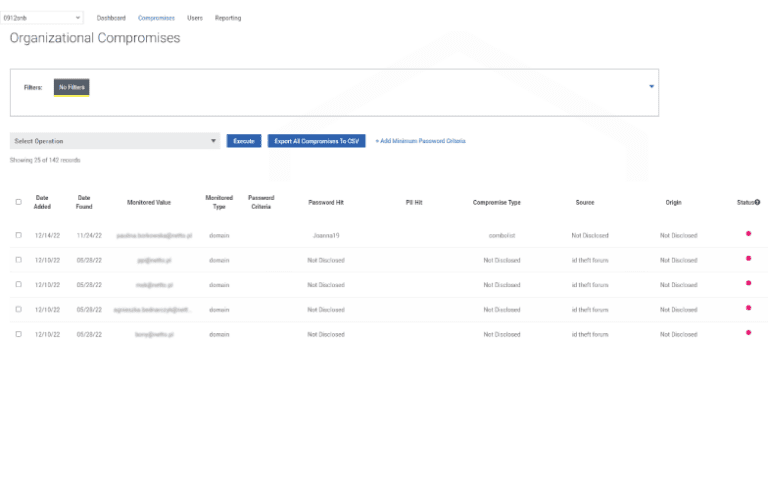
Dark Web ID
Uncover compromised credentials from all corners of the dark web within seconds with this dark web monitoring and compromise alerting tool.
Discover Dark Web ID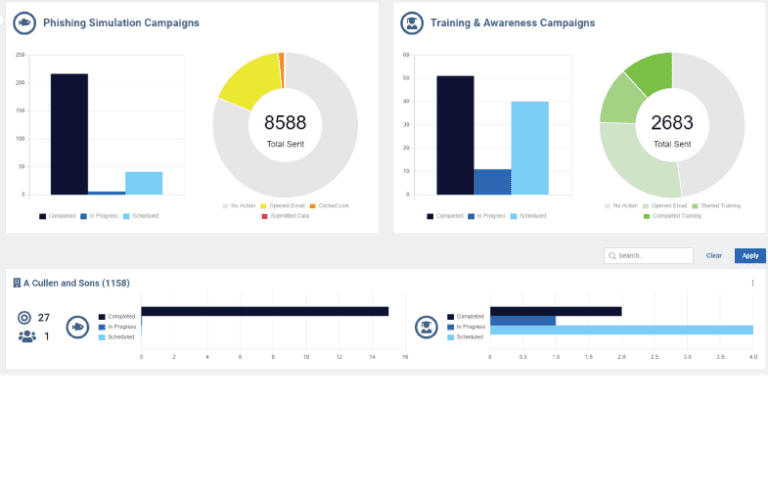
BullPhish ID
BullPhish ID's effective security awareness training and phishing simulations empower employees to be more secure.
Discover BullPhish ID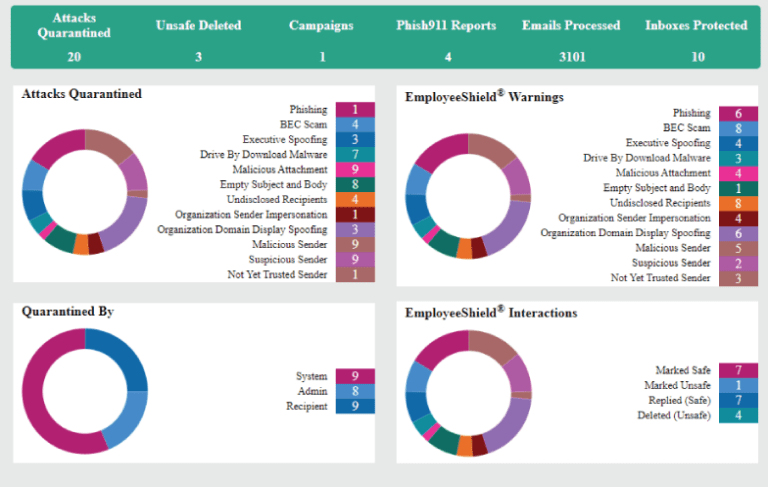
Graphus
This AI-powered email security solution stops and learns from threats other solutions miss, significantly reducing the risk of threats slipping through.
Discover Graphus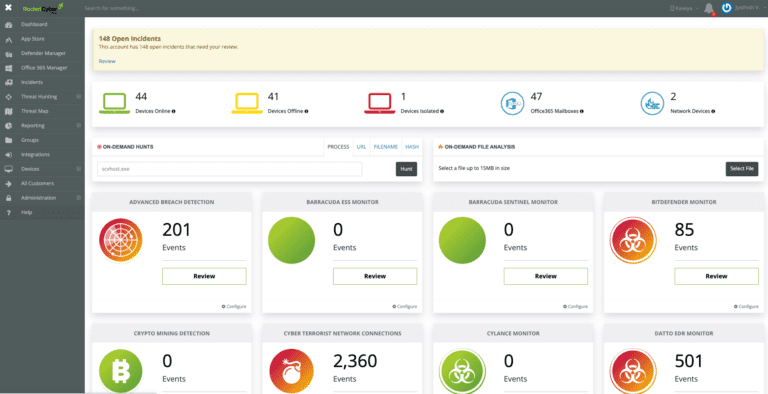
Managed SOC
By leveraging our team of cybersecurity experts, you can provide MDR support — even if you lack the expertise.
Discover Managed SOC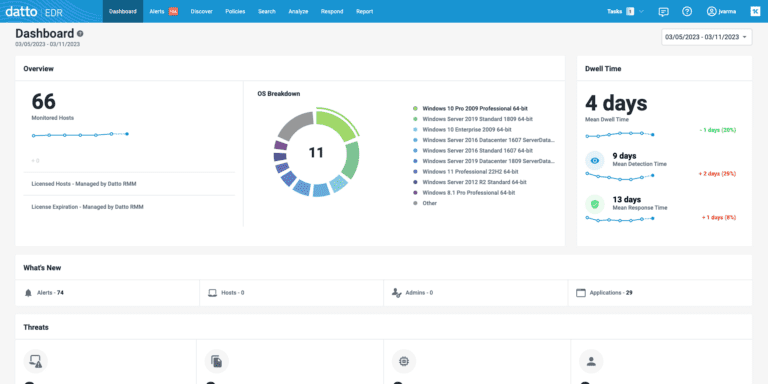
Datto EDR
Built-in continuous endpoint monitoring and behavioral analysis streamline endpoint detection and response (EDR).
Discover Datto EDR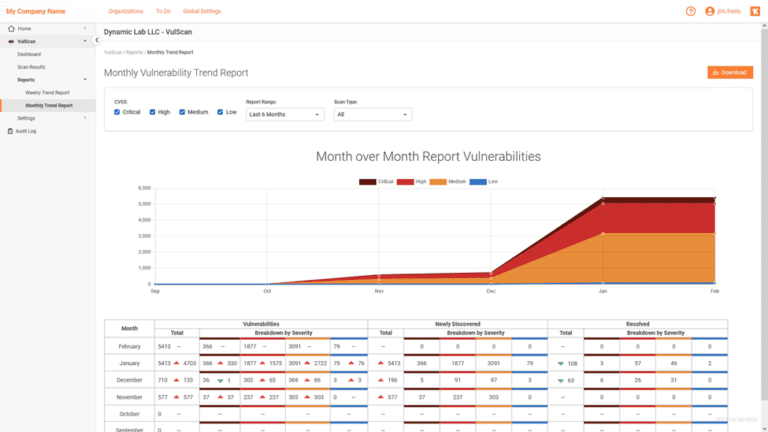
VulScan
VulScan identifies IT vulnerabilities in your network by automatically scanning and prioritizing remediations, so you can resolve issues rapidly.
Discover VulScan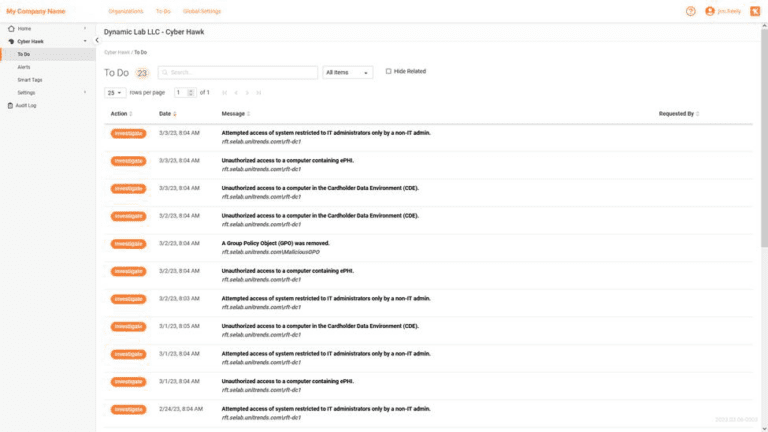
Cyber Hawk
Cyber Hawk detects and alerts on suspicious changes, misconfigurations and activities across your network that create vulnerabilities in your systems.
Discover Cyber Hawk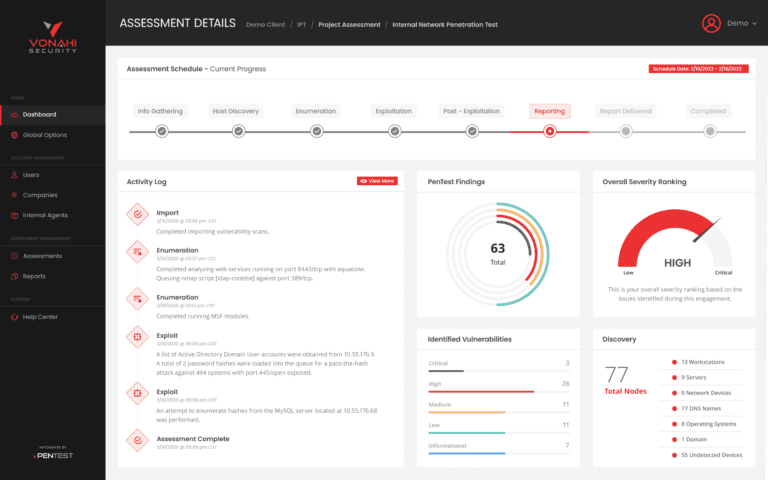
Vonahi vPenTest
Automated network penetration testing that meets compliance, proactively helps organizations reduce risk, and allows for monthly testing without breaking the bank.
Discover VonahiRemove the Complexity of Multi-Layered Security Offerings
With the ever-increasing number of devices connected to IT networks, the pathway for malicious actors is expanding by the second. A trustworthy defense requires sophisticated security tools that can detect and address even the most advanced cyberthreats before they become a problem. Kaseya’s Security Solutions provide full coverage while also being simple to manage, providing IT Professionals both peace and ease of mind.
The IBM cost of a Data Breach 2022 report pegs the cost of a data breach at $4.4 million and the average cost of a ransomware attack at $4.54 million.
is the average spend of SMBs to restore normal business in the wake of a cyber attack.
of SMBs will experience business disruption as a result of a security event in the next 3 years.
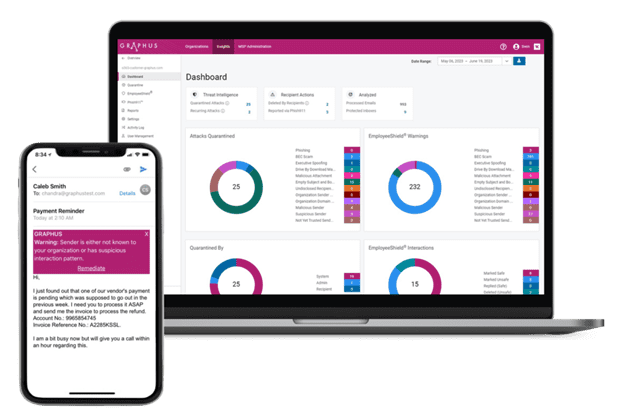
Protect Users With End-to-End Security
We offer an array of modern security tools to safeguard organizations from phishing, ransomware, credential compromise, and other advanced threats and cybercrime businesses encounter daily. Affordable and effective, our tools stop breaches before they can occur while ensuring the ease and efficiency needed by already overworked IT Professionals.
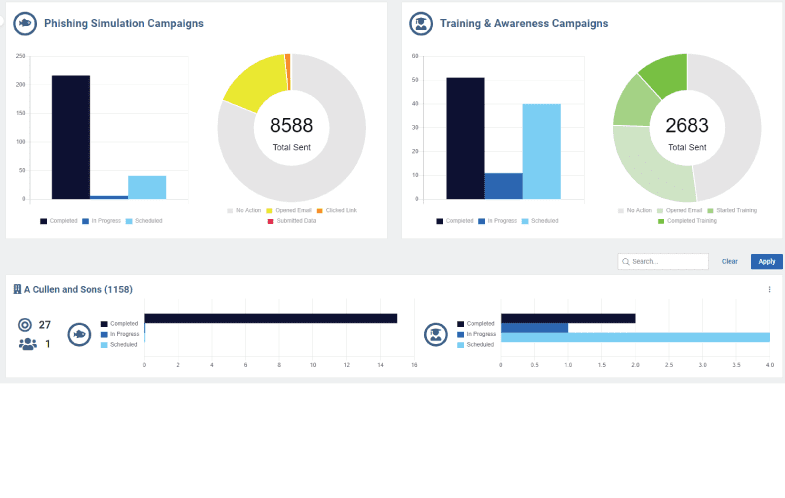
Defend Against the Latest Cyber Attacks
To ensure the cyber safety and continuity of your operations, you need a multi-layered security strategy. The Kaseya Security Suite solutions not only affordably protect your main attack surfaces, but also work together to alleviate your IT team’s workload.
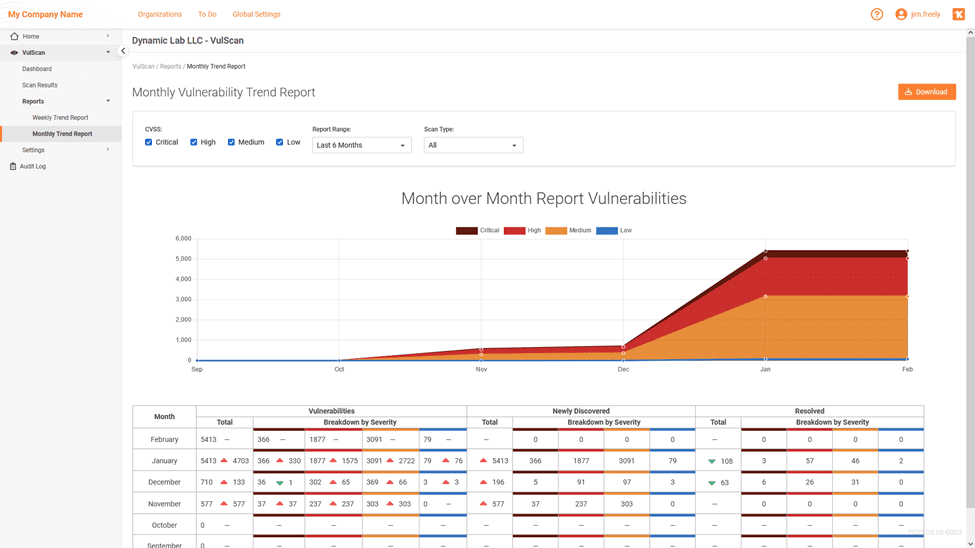
Gain Visibility & Eliminate Network Blind Spots
You can’t protect what you can’t see. Knowing what assets are on your network and their status is critical to stopping cybercriminals from exploiting misconfigurations and vulnerabilities. Immediately see when unauthorized applications, users or devices join your network, and lock them down before harm is done.
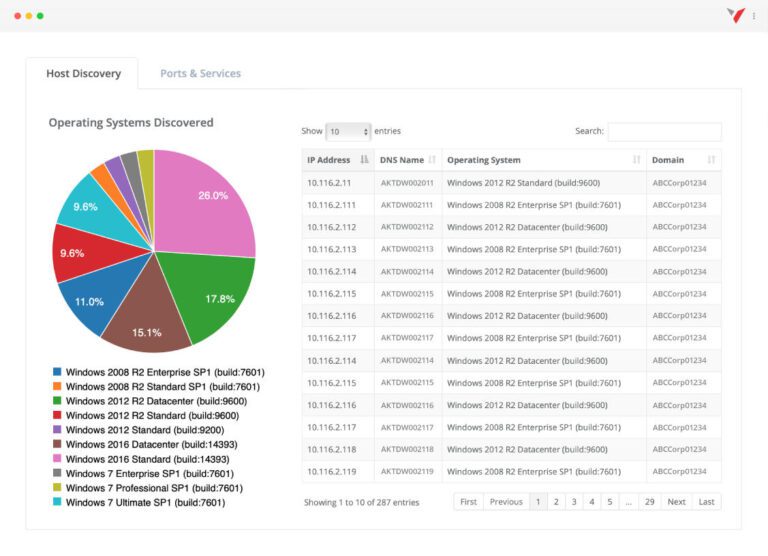
Vonahi
Continuous network penetration testing with real-time visibility to save time and money while still allowing for complete testing control.
Featured Workflow Integrations for Security Solutions
Below are some of the most popular IT Complete Security Suite integrations.
Dark Web ID & BMS
An alert is seamlessly created in BMS whenever Dark Web ID finds a new compromise for the monitored value, resulting in faster mitigation.
BullPhish ID & IT Glue
This integration leverages the IT Glue API for seamless customer onboarding to BullPhish ID. It imports organization names and contacts, reducing the need for manual entry.
Dark Web ID & Autotask
Autotask users can configure Dark Web ID exposure alerts to instantly create tickets within their PSA console, allowing for faster alert mitigation.
Datto EDR & Datto RMM
Protect endpoints from threats that may go undetected with integrated policy management, reporting and centralized alerts between Datto EDR and RMM.
Why IT Professionals love Kaseya's IT Complete
“We decided to go with Kaseya because it seemed to be the most complete solution. Other solutions we looked at, they’d have one part or the other, but with Kaseya we have it all”