Information Security
Kaseya employs a Chief Information Security Officer (CISO) who reports to the Chief Operating Officer (COO), a direct report of Kaseya’s Chief Executive Officer (CEO). The Kaseya CISO is a senior business leader who is empowered to maintain a culture of security across the organization and build capabilities that assure information security and cyber resilience for Kaseya and our customers.
The CISO is responsible for creating and maintaining an organization with documented roles and responsibilities. This organization consists not only of security staff that report directly through the CISO, but also security staff embedded within key business functions. This agile staffing model ensures that staff are placed in the right locations within the business to drive robust security requirements and risk reduction efforts necessary to keep Kaseya and our customers safe.
| Program Management | Governance Risk & Compliance | Network & System Security | Data Protection | Security Operations | Identity & Access Management | Application Security | Security Incident Response | Business Continuity | Physical & Personnel Security |
|---|---|---|---|---|---|---|---|---|---|
| Business Alignment | Policies, Procedures, & Standards | Network Security | Data Classification | Vulnerability Management | Identity Management | Secure SDLC | Incident Response Planning | Business Continuity Management | Physical Security |
| Security Strategy Roadmap | Security Awareness & Training | Network Access Management | Encryption | Penetration Testing | Authentication Authorization | Secure Design & Coding | Investigations | Business Impact Analysis | Personnel Security |
| Budget Management | Information Risk Governance | Remote Access | Key Management | Asset Management | User Provision / Deprovision | Secure Code Review | Computer Forensics | Disaster Recovery | Records Destruction & Disposal |
| Resource Management & Staffing | Security Metrics | Endpoint Protection | Data Leakage Protection | Change Control | Privileged Access Management | Application Penetration Testing | Discovery Support | Business Continuity Testing | User Enforcement |
| Enterprise Security Architecture | 3rd Party Risk Management | Mobile Security | Secure Messaging | Security Event Monitoring | Network Account Management | Breach Response | |||
| Compliance | Secure File Transfer | Threat Intelligence | |||||||
| Audit | Cloud Data Security | ||||||||
| Privacy |
Frameworks
The information security program we maintain must be verifiable against well-known and understood security frameworks to provide the highest level of assurance to our customers and stakeholders.
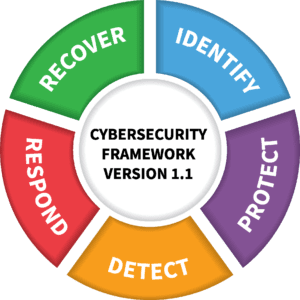
NIST Cybersecurity Framework
In support of our cyber resilience mission, Kaseya has selected the NIST Cyber Security Framework as the foundational framework against which we measure the scope and maturity of our information security program. The people, process and technology capabilities we build are aligned to this framework and support industry leading security program maturity.
Building Security in Maturity Model (BSIMM)
Kaseya selected the Building Security in Maturity Model (BSIMM) application security framework to drive industry leading software security practices into IT Complete modules and services.
The adoption of this framework ensures that IT Complete modules follow the leading software security activities through periodic assessment and validation by an independent third party.
Governance, Risk and Compliance (GRC)
The Kaseya Information Security program has a staffed GRC function responsible for processes and activities that govern security throughout the organization. This function’s broad mandate includes assuring security compliance of Kaseya and our IT Complete modules; evaluating cyber risks; partnering with human resources on personnel security; security education and workforce training; and maintaining and communicating security policies. This function works closely with other information security teams to audit and assess the operation and effectiveness of internal controls, as well as assure that response and recovery plans are current and actionable.
Policies and Plans
Kaseya maintains a comprehensive set of information security policies and plans that align with the NIST Framework and set the foundation for the formal Information Security program:
- Security Policy
- Acceptable Use Policy
- Incident Management and Response Plan
- Patch Management Policy
- Vulnerability Management Policy
- Data Governance Policy
- Risk Management Policy
- Third Party Risk Management Policy
- Business Continuity Plan
- Disaster Recovery Plan
- Encryption Policy
- Change Management Policy
- Asset Management Policy
- Electronic Data Disposal Policy
- Software Development Lifecycle Policy
- Physical Security Policy
Policies are reviewed and approved by Kaseya senior management, created and maintained annually by the GRC team with direct input and oversight by the Kaseya CISO and communicated to staff with annual review and acceptance requirements.
These policies are reviewed and audited multiple times annually as part of the AICPA SOC 2 audits of Kaseya IT Complete modules.
Security Compliance
The Kaseya GRC team conducts multiple internal audits annually to assure that internal controls continue to operate effectively and maintain a continuous state of external audit readiness.
The vigorous nature of our internal preparedness has led to a history of exception-free SOC 2 Type II audits for a wide set of IT Complete modules. This superlative result demonstrates Kaseya’s long-running commitment to an effectively operating security program.
In addition, this team supports Legal and Privacy Compliance efforts and helps to assess and prepare Kaseya to achieve additional security compliance standards, as deemed necessary by the company and its customers.
Security Education and Awareness
Staff receive security education and training upon hire, annually and on an as-needed basis. Training covers a broad set of subjects including safe computing, acceptable use, ransomware, endpoint security, safe browsing, credential security, social engineering and phishing, amongst other topics relevant to the workforce. Specialized staff receive additional role-specific training as appropriate.
Kaseya employees are frequently tested to assess awareness of and susceptibility to social engineering and phishing attacks. If a staff member engages with a simulated phishing message, additional training will be provided to improve awareness and reinforce security best practices.
Kaseya is proud to use the Graphus and BullPhish ID IT Complete modules to provide this critical training and testing to our staff.
Business Continuity Planning (BCP) and Disaster Recovery (DR)
Kaseya’s Information Security program staffs a BCP and DR function to maintain an accurate inventory of critical business processes and their dependencies, tolerance to disruption, recovery objectives and continuity or contingency plans. This is accomplished through business impact assessments (BIAs) that drive the continuity and recovery plans that are built and maintained with process and technology owners.
Kaseya periodically tests continuity, contingency and recovery plans during routine maintenance and through tabletop exercises with expert staff.
By prioritizing our most critical business processes and maintaining current and documented recovery plans, Kaseya ensures organizational resilience to incidents that may affect the availability of key processes on which we depend to deliver exceptional service.
Third Party Risk Management (TPRM)
As the risks posed by threat actors who exploit weaknesses in business relationships and technology supply chains become greater, companies must maintain a strong security posture and requirements for critical vendors, suppliers and business partners.
Kaseya’s TPRM function assesses the security practices of the company’s network of new and existing third-party providers with the goal of creating a network of suppliers that possess reasonable and verifiable security postures and strong contractual security requirements that govern our relationships. This function uses a mix of assessment techniques that include questionnaires, interactive interviews, onsite visits and technology solutions that conduct continuous security posture assessments.
When the TPRM team has identified a critical security vulnerability that may impact key suppliers, Kaseya leverages continuous security posture monitoring solutions to identify potentially impacted vendors and prioritize engagement with them.
Personal Security
The security of the overall Kaseya organization and IT Complete modules is dependent on trusted internal and external parties. Kaseya employees are subject to background checks during the hiring process, where jurisdictionally permitted, and as needed based on job level, role, and responsibility. In addition to reviewing and acknowledging security policies and the business code of conduct prior to commencing employment, staff also receive training related to company security policies and information security expectations. Account creation and termination, access permissions and removal processes are linked to onboarding and offboarding procedures that govern hiring and termination.
Physical Security
Kaseya maintains physical security policies and procedures that govern corporate offices, manufacturing sites and datacenter facilities used to deliver Kaseya IT Complete modules and services. Information security, facilities and datacenter operations teams are responsible for overseeing that adequate logical and physical access controls are deployed for each facility in accordance with policy. Teams periodically audit facilities and controls capabilities to verify they are being adequately tested, maintained and monitored. Controls capabilities include access control systems, cameras and recordings, temperature and humidity sensor management, visitor procedures, generator and UPS failover testing, amongst others. These validation activities provide confidence that facilities are resilient to failure and only accessible to appropriate, authorized individuals.
Application Security
A key objective of Kaseya’s Information Security Strategy is to deliver best-in-class product security, specifically with respect to the software security of IT Complete modules.
Therefore, the information security team drives software security processes and technologies into the formal software development lifecycles that govern product development. These foundational activities, supported by dedicated application security experts and software security champions, include threat modeling, static and dynamic analysis, security regression testing, secure code review and penetration testing.
Offensive Security
Kaseya employs a team of full-time security researchers who are certified in web application hacking, penetration testing, exploit research and development, fuzzing and advanced social engineering.
The offensive security team adds an unparalleled level of software security assurance through daily activities, some of which include:
- Product-based Penetration Testing – searching for weaknesses that may have been missed by other technologies and processes.
- Service-based Penetration Testing – selecting a specific network-accessible service and assessing all instances of that service for vulnerabilities across the entire operating environment.
- Objective-based Red Team Exercises – seeking to accomplish a specific mission, through any means that would be available to a threat actor.
- Attack Surface Mapping and Management – looking for exposed services and vulnerabilities that exist in the grey space between products.
- Advanced Social Engineering Tests – imitating advanced targeted attacks and replicating the techniques and procedures used by highly motivated threat actors.
- Exploit Research and Development – identifying, creating proofs-of-concept and disclosing exploits in software and technology (including supply chain products) used to deliver IT Complete modules and services.
- Purple-teaming Activities – testing cyber defenses and response capabilities with security operations center and threat management teams.
Application Security Verification Standard (ASVS)
Quality of penetration tests are affected by test scope, test duration, assessor skill, and breadth of attack method coverage. To achieve consistency and quality in our pentests, Kaseya follows the requirements set forth by the Open Web Application Security Project (OWASP) Application Security Verification Standard (ASVS). Our qualified and talented offensive security team staff conducts tests that meet ASVS Level 2 requirements, which are recommended for most applications and websites with advanced security needs.
This focus on penetration testing quality provides Kaseya with confidence in the security of IT Complete modules.
For the most up to date information on ASVS please visit: https://owasp.org/www-project-application-security-verification-standard/
Building Security in Maturity Model (BSIMM)
Kaseya Software Security Initiative (SSI) maintains a Software Security Group (SSG) comprised of a network of senior software engineering leaders, senior software development staff, information security leaders and embedded software security champions from across the organization.
The SSG has universally adopted the Building Security in Maturity Model (BSIMM) as its primary application security framework, driving industry leading software security practices into the development and maintenance of IT Complete modules.
BSIMM, unlike other application security frameworks, is updated annually as the software security activities observed across a network of over 400 member companies are assessed. The dynamic nature of benchmark activities, and the fact that the framework is independently assessed, appeals to Kaseya as we strive to build and maintain leading software security practices.
Kaseya’s adoption of BSIMM and our goal to achieve and maintain an average high-water mark maturity score of level 2 assures continuous improvement within our organization’s software security programs.
Vulnerability Disclosure Program and Bug Bounty
As with any software development, it is possible, despite advanced and layered application security activities implemented for IT Complete modules, that vulnerabilities may escape.
Identification of these escaping vulnerabilities may occur by customers or security researchers. Seeing the value in collaborating deeply with our customers and the security researcher community, we welcome responsible, professional and discretionary disclosure through our active Vulnerability Disclosure Program (VDP).
VDP programs are a common and safe way for anyone who finds a vulnerability to report it to us in a responsible way that affords a reasonable amount of time for issue validation and correction before public disclosure.
Our VDP has a Bug Bounty component. This is beneficial as bounties are open to anyone, unlike in a Private Bug Bounty that limits participation. We may offer monetary recognition for vulnerability reports that have a significant business impact on our customers, products or services.
Kaseya may choose to recognize exceptional contributions to the security of IT Complete modules and resulting risk reduction for all our customers by adding the discloser(s) to a Hall of Fame.
Threat Informed Cyber Defense
We must maintain an understanding of threat actors and their tradecraft to understand the cyber risk landscape that we operate within, and how it might evolve in the future. We use cyber threat intelligence to gain an understanding of threat actors and apply that knowledge to the cyber defense and intrusion monitoring capabilities we employ within our security program. This threat informed cyber defense is critical to effectively manage cyber risk for us and our customers.
Threat Management
When designing cyber defenses, it is important to know the threat actors that may seek to impact your organization.
We need to maintain continuous awareness of threats by seeking to identify, assess, classify and respond to threats in a structured way. Kaseya’s full-time threat management analysts collect, consume, share and craft actionable reports from strategic, tactical, technical and operational cyber threat intelligence (CTI) from open-source intelligence (OSINT) and commercial intelligence sources.
The result is an extensive understanding of the threat profile for our industry and our company and the tactics, techniques and procedures (TTPs) that threat actors may attempt to leverage against us. With threat management, we maintain a level of threat awareness that makes the information security program more agile to threats and vulnerabilities and makes the program more cyber resilient overall.
Intrusion Monitoring
In a world that assumes breaches will occur, we must maintain a constant state of readiness to respond to cyber-attacks and intrusions.
Kaseya staffs an in-house security operations center (SOC) team and a security engineering team to manage all activities that relate to intrusion monitoring. This is accomplished by using a combination of internally deployed and maintained security information and event management (SIEM) technology, and third party managed detection and response (MDR) providers.
This layered approach allows us to analyze for intrusions across clouds, networks, endpoints and SaaS logs for a comprehensive view into cyber attacks.
Kaseya’s security engineering function makes sure that the technologies used by the SOC are operating well. They support the SIEM with log source ingestion and parsing as well as detection engineering.
Kaseya SOC responds 24×7 to security events deemed worthy of investigation by intrusion monitoring rules and alerts from the SIEM and the MDR provider. Should a security event be deemed valid and significant, then an Incident is declared in accordance with Kaseya’s Incident Management and Response policies.
Incident Management and Response
Kaseya maintains an Incident Management and Response policy and procedures that are modeled on the best practices guidance for handling the lifecycle of an incident response efficiently and effectively as documented by NIST in special publication 800-61.
Kaseya maintains documented response procedures and playbooks for incident declaration, escalation, containment and recovery to assure efficient and effective handling and remediation of security incidents. We assure that staff most likely to identify and initially respond to potential security incidents receive first-responder training.
We retain services with a reputable incident response firm that can provide immediate digital forensics and incident response support (DFIR) should Kaseya’s internal incident response team need augmented expertise, support or capacity to respond.
For the most up to date information on NIST SP 800-61, please visit https://csrc.nist.gov/publications/sp
Purple Teaming
Kaseya security operations center, offensive security and threat management teams periodically conduct coordinated tests and exercises that emulate tactics, techniques and procedures (TTPs) used by threat actors. These exercises allow us to observe the operating effectiveness of our protective and detective controls and processes. Purple team activities provide additional assurance, outside of audits, that the core intrusion monitoring processes are working well, and give us an opportunity to safely identify gaps and areas for improvement in a coordinated and thoughtful way. When there are new or emerging TTPs identified by threat management, we will seek to emulate those and baseline our environment’s defense capabilities. The purple team may conduct this analysis via coordinated exercises or with adversary emulation tools that allow for quick and continuous automated TTP testing.
Hunt Teaming
Periodically, the threat management function will identify a set of behaviors or indicators associated with threat actors and their tradecraft that are potentially applicable to our operating environments. The threat analysts will work directly with the security operations team to proactively search across our environments for signs of these behaviors and indicators – an activity known as threat hunting.
Cyber Hygiene
Cyber hygiene occurs through consistent execution of fundamental IT capabilities and routine processes that maintain operating health. A key objective in Kaseya’s Information Security Strategic plan is to continuously assure cyber hygiene, which is a commitment to continued maturation and excellence of foundational capabilities that protect users, systems, networks, software and data.
Asset Management
Kaseya maintains inventories of internal IT (corporate) and customer production assets, including data, software, and both physical and virtual network connected devices. Maintenance of these inventories permits us to maintain constant awareness of the scope of assets that must be monitored and protected.
Assets are classified and inventoried in accordance with company policies. Asset inventories are maintained and periodically audited to assure relevancy and accuracy, given their critical nature, and constant reliance on them for critical protection processes that assure essential cyber hygiene is maintained for systems and data, that we own, or are custodians of.
Vulnerability Management
Kaseya maintains policies and procedures to assure that vulnerabilities in system, software and network assets are effectively identified, tracked and mitigated.
We take a risk-based vulnerability management approach to prioritize remediation activities, which is informed by data from a variety of commercial and open-source vulnerability scanners, security researchers, offensive security team activities, and cyber threat intelligence from our commercial, open-source and federal government sources.
The combination of broad vulnerability data, threat data, and a detailed understanding of the potentially exploitable attack surface of a vulnerability allows us to understand the cyber risk that a distinct vulnerability may present.
This approach also allows us to expedite response to Zero Day and N-Day security vulnerabilities. Using rapid assessments we derive a detailed understanding of vulnerability severity, exploitability, exploit difficulty, threat actor, weaponization, potential exposures and impacts of the vulnerability. These rapid assessments produce action items that mitigate cyber risk quickly by expediting patching in a risk prioritized manner.
These capabilities inform other facets of our security program, such as third-party risk management, to assure our critical business partners are responding appropriately, and intrusion monitoring, to assure we have effective monitoring in place to detect attack attempts using such vulnerabilities.
Patch Management
Kaseya maintains policies and procedures that assure security patches to system, software, and network assets are effectively identified, tracked and applied. Patches are qualified, tested and released in a manner that assures both security and availability of the assets, and critical business process or IT Complete modules they support.
Kaseya leverages a set of solutions to help automate the safe deployment of patches to managed endpoints. Regular patching processes are designed to assure timely distribution to applicable assets, but we also maintain an emergency patching process which allows us to prioritize work efforts to accelerate testing, distribution and application of patches in exceptional circumstances.
Change Management
Kaseya maintains policies and procedures that assure changes to system, software and network assets are documented, reviewed, authorized, planned, deployed and monitored. Changes are tested and released in a manner that assures both security and availability of the critical business process or customer products they support. They are governed by formal change management processes and procedures that adhere to the change management policy.
Changes are classified based on factors, such as the change scope, assets affected, duration of maintenance, impact to service, security implications, complexity of implementation or recovery and more.
Classification dictates when a change can be made, stakeholder notification requirements and whether the change requires review and approval.
Multiple times per year an audit of changes is conducted to identify and correct potential issues with adherence to change management practices.
Endpoint Protection
Kaseya maintains endpoint protection and security protection capabilities that assure secure configuration, operation, maintenance, and monitoring of corporate and production computing assets.
Technology and process capabilities include use of endpoint protection solutions (e.g., anti-malware or endpoint detection and response) configuration management solutions and data encryption.
Those solutions are centrally managed by Kaseya information security, internal IT and production engineering teams.
Identity and Access Management (IAM)
Kaseya Information Security works with Internal IT to assure that staff systems accounts follow a formal process for access provisioning and decommissioning that is tied to Human Resources hiring and termination processes. Each user is given a unique credential and required to set up both a strong password and Multi-Factor Authentication (MFA). Kaseya maintains centrally managed SSO platforms that are hardened to provide secure access to systems and services. Access is provided on a need-to-know basis enforcing least privilege and is based on role. Periodic audits of accounts and access are conducted to ensure that routine hygiene processes are operating well.
Email Security
Kaseya Information Security works with Internal IT to assure that secure protocols and configurations are maintained on corporate email solutions. Email protection controls include, but are not limited to, email in transit encryption (e.g., STARTTLS and SSL/TLS), commonly malicious attachment type blocking, MFA for email platform access, disabling less secure mail access protocols (e.g., IMAP, etc.), anti-spoofing solutions (e.g., SPF, DKIM, and DMARC) and deploying additional layers of email security filtering to reduce email-borne threats (e.g., phishing, spam, etc.).
Network Security
Kaseya Information Security department partners with IT and network engineering to deploy and maintain network security controls and processes that assure threat prevention and reliable access control Kaseya maintains a fleet of modern user-context and application-aware firewalls that are capable of advanced threat detection and prevention in encrypted and unencrypted traffic to protect our corporate networks and users.
Production networks use a mix of physical, virtual and cloud networking capabilities to implement a network security architecture that designates distinct security zones to control access to and from key infrastructure systems, while still allowing for world class product integration. Access is governed by criticality of a system, data sensitivity classification, and risk.
Network vulnerability and patch management processes are maintained. Vendor advisories are monitored, and networking appliances are scanned for vulnerabilities. Updated network operating systems are applied at least annually, or more frequently when an advisory or vulnerability necessitates it.
