Increase IT Efficiency and Get More Done
Demand for IT services has gone up dramatically. How can your IT team keep up without increasing costs?
It’s all about increasing IT operational efficiency. Here are a few strategies you can use:
- Automate IT processes
- Remotely monitor and manage endpoints, including work-from-home (WFH) users’ computers
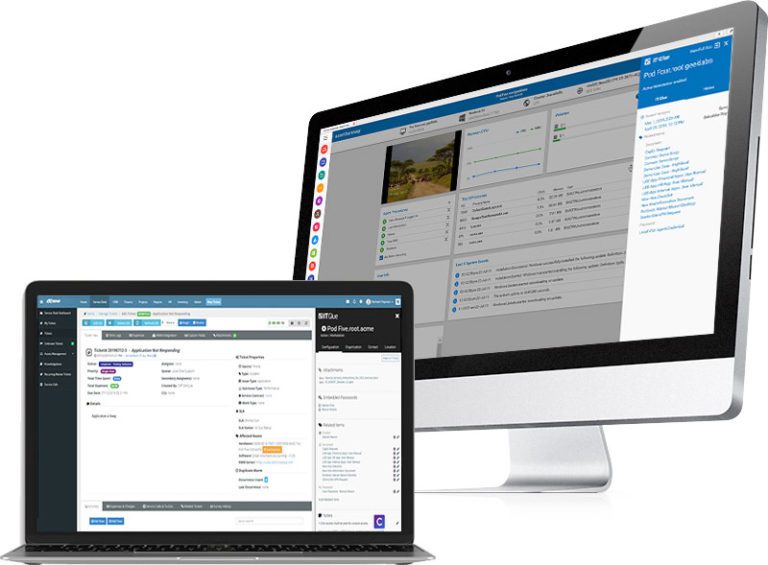
- Leverage seamless workflow integrations between your Endpoint Management, Service Desk and Knowledge Management solutions – Kaseya VSA, Vorex and IT Glue
Increase IT technician efficiency by 25 percent or more! Have more time and budget for strategic IT projects that drive business growth.
“Our IT department is a staff of 6 and we have about 1,100 users. We’re always looking for ways to be more efficient and Kaseya VSA helps us do that in a big way.” – Larry Taylor, Senior Network Engineer for Whitfield County, GA
Enhance IT Security
Cyberattacks have gone up by more than 400 percent this year. What can your IT team do to improve the security posture of your business?
Enhance IT security and reduce your risk with Kaseya VSA by:
- Automating software patch management and vulnerability management
- Deploying and managing Antivirus and Antimalware solutions
- Managing Backup and Disaster Recovery
Maintain IT System Availability
Keeping IT systems up and running is the top priority for IT teams. Make their job easier with Kaseya VSA, Vorex and IT Glue.
Increase system availability by:
- Monitoring and managing all your servers, desktops and laptops, as well as your (SNMP) network devices.
- Auto-remediating IT incidents and quickly closing service tickets with VSA and Vorex.
- Quickly finding the incident root cause with VSA’s Network Topology Map.
Manage All Essential IT Functions With Kaseya’s IT Management Platform
Kaseya VSA is a leading endpoint management solution. VSA is the foundation of our IT Complete suite of IT management products.
Monitor and manage endpoints, patch and deploy software, and automate IT processes with VSA.
Get more done faster with VSA agent procedures.
Kaseya Vorex is a powerful helpdesk solution for midsize businesses. Create, manage and resolve all your IT service tickets with Vorex.
Auto-remediate service tickets using VSA agent procedures right in Vorex.
Quickly troubleshoot and resolve IT incidents with direct access to VSA remote management features.
Manage and grow your business with the world’s leading IT documentation, knowledge and configuration management software. IT Glue is integrated with both VSA and Vorex to provide IT asset configurations, and related IT procedures right in the VSA and Vorex UI.
BudgetFuel for your IT Department
Increase your IT operational efficiency through automation and seamless workflows. Get more done with less! Free up budget for IT innovation.
Reduce IT management tool costs with Kaseya’s IT Complete suite of products. Leverage one vendor and have the freedom to add products to your stack as your needs change.