Small and medium sized businesses (SMBs) have become more vulnerable to cyber attacks. About 43 percent of cyber attacks are aimed at SMBs since they do not always have the best defenses in place to secure their business.
The primary challenges for most SMBs are limited IT budget for security tools and the lack of cybersecurity expertise — for monitoring and managing the security of the IT infrastructure.
The Internet of Things (IoT) and unsecured IoT devices are also proving to be a huge risk for SMBs. In 2017, 50,000 cyber-attacks were targeted at IoT devices, an increase of 600 percent from 2016 and the number of IoT-driven malware attacks surpassed 121,000 in 2018.
Although SMBs may not have the same access to resources and manpower as large enterprises, they can improve the security their business with an effective IT security strategy.
Here are five ways SMBs can protect their business from cyber attacks.
Top 5 Ways to Improve the Security of Your Business
1. Perform a security assessment
Assessing your company’s security threats is the first step towards keeping your IT environment secure. Security assessments include checks for vulnerabilities in your IT systems and business processes, as well as recommending steps to lower the risk of future attacks. Security assessment tools provide a way to identify and resolve security issues.
RapidFire Tools, a Kaseya company, offers a security assessment solution called ‘Network Detective’ that scans your network and gives you a security assessment score:
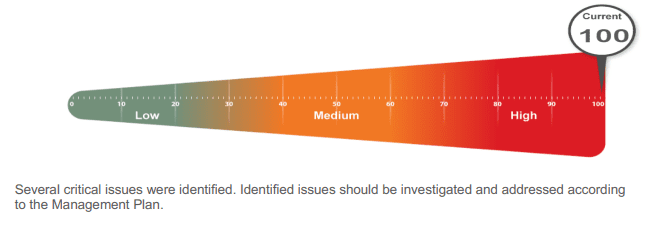
Security Assessment Score
Network Detective also identifies issues such as:
- External vulnerabilities that could be potential security holes that would allow hackers access to your network and
information - System protocol leakage- outbound protocols that shouldn’t be allowed
- Lack of web browser controls
- Wireless network security issues
- Network share permissions, and more
2. Automate software patch management to remediate software vulnerabilities
WannaCry, the cyberattack that infected more than 230,000 computers in over 150 countries in 2017, could have been avoided with a simple patch. About 80 percent of security breaches in 2017 was the result of poor patching.
Maintaining a robust patch management process is critical for the security of the business. But many SMBs do not patch vulnerabilities in a timely manner despite being aware of the consequences. SMBs usually have a small, multi-function IT team. This makes it difficult for them to afford the resources and time for manual patch management. Automated patching is a cost-effective alternative to the drain of manual patching. With automation, you can easily achieve the goal of remediating critical vulnerabilities by applying patches within 30 days of first availability.
Automated patch management is a core capability of Kaseya VSA. It simplifies patching and reporting for Microsoft, Mac OS and third-party applications across all your servers, workstations and virtual machines.
With Kaseya VSA:
- You have complete visibility into your IT infrastructure landscape which makes it easier to locate machines with vulnerabilities.
- You can schedule the deployment of patches on any machine in the environment.
- You have the ability to override a rejected update and redeploy the patch.
- Microsoft patches come from the online Microsoft update catalog—automatically. Recently, Microsoft provided a critical patch for a remote code execution vulnerability called BlueKeep (CVE-2019-0708) in remote desktop services which had the same threat level as WannaCry. Customers with VSA would have had automatic patch updates in place.
3. Implement multi-factor authentication (MFA)
About 81 percent of data breaches are mainly caused by stolen or weak credentials. Many users reuse passwords or use weak passwords such as “123456” and “password” – these were used by 23.2 million and 3 million accounts, respectively. This makes systems vulnerable to brute force attacks in which the attacker systematically tries all possible passwords and passphrases until the correct one is found.
Multi-factor authentication adds an extra layer of security to the login procedure beyond using just a password. The most common form of MFA is two-factor authentication (2FA). 2FA solves the password problem by requiring something users know- username + password, and something they have- a token or smartphone app.
A few companies are moving away from passwords altogether —e.g. Microsoft, with biometric technology used in combination with MFA.
Kaseya AuthAnvil is an identity and access management (IAM) solution which provides two-factor authentication to improve security. It has an authenticator app for iPhone and Android devices. It also provides Out of Band Authentication (OOBA) which refers to an authentication process that utilizes a communications channel that is separate from that used by the client and server trying to establish an authenticated connection.
4. Detect and respond to insider threats
The 2019 Verizon Data Breach Investigations Report (DBIR) shows that 34 percent of breaches involve internal actors. Insider threats not only involve malicious attacks, but also the negligent use of systems and data by employees.
To protect against these threats, organizations need to quickly and accurately detect, investigate and respond to issues that could be indicators of insider attacks. Insider threats require specialized tools. Common antivirus and anti-malware (AV/AM) tools usually won’t be effective against these threats.
Cyber Hawk, a RapidFire Tools product detects insider threats by monitoring:
- Unauthorized logins
- New apps installed on locked-down computers
- Users that recently got admin rights to a device
- New devices on restricted networks, and more.
With Cyber Hawk, you can set and enforce as many security policies as you want. You can also automate scanning and leverage Security Policy Violation Based Alerting for instant alerts. Cyber Hawk combines machine learning and intelligent tagging to identify anomalous activity, suspicious changes and threats caused by misconfigurations.
5. Backup all your systems, from on-premises to cloud, to protect against ransomware attacks
Picture a scenario: One fine day you are working on your system and you realize something is not right. Your computer begins to slow down and you are unable to access your files.
You are now completely locked out of your system with a message displayed in front of you.
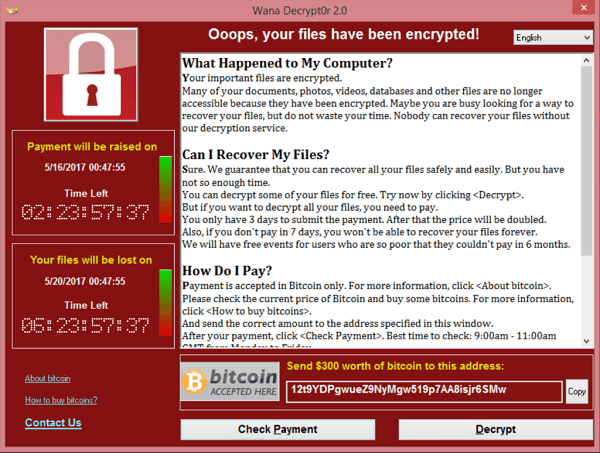
Screenshot of the ransom note left on an infected system – Sourced from Wikipedia
Your worst fears have come true. You are the victim of a ransomware attack.
Ransomware attacks can be crippling to a midsize business that does not have a proper backup strategy in place. And, those that have backups in place are also in danger of the backup itself being infected. With evolved malware strains attacking systems, being absolutely secure has become a thing of the past. There is always a weakness in the landscape.
Kaseya Unified Backup (KUB) brings together the world’s best backup, ransomware protection, cloud-based storage and business continuity and disaster recovery (BCDR) solutions. It works on-premises and for IaaS and SaaS applications.
With KUB you can be assured that every file is inspected during each backup for ransomware infections to ensure “clean” recoveries.
To learn more about improving your IT security strategy, watch our on-demand webinar Unify Security with Unified IT Management.





