Patch management and vulnerability management play a critical role in endpoint security. The process includes discovering assets in the network, scanning the assets and reporting on security vulnerabilities associated with software installed on those devices. The remediation of the security vulnerability involves patching the software on all of the systems where its installed. If patches are not applied to systems in a timely manner, your IT infrastructure can be compromised, and subject to attacks.
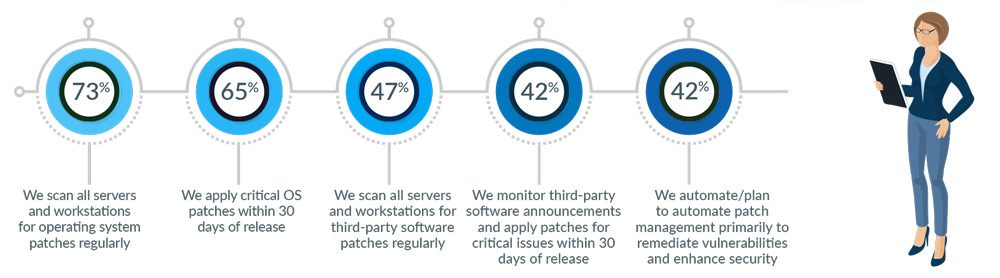
In the 2019 Kaseya State of IT Operations Survey, nearly three-quarters of participants stated that they scan all servers and workstations for operating system (OS) patches, whereas about 47 percent said they scan all servers and workstations for third-party software patches regularly.
While most businesses are aware of the importance of patching, many lack the proper tools and automation necessary to carry out patching in a timely manner. The sheer number of patches means that manual processes can’t keep up. In 2018, more than 22,000 software vulnerabilities were disclosed. A patch is made available at the time of disclosure for the vast majority of vulnerabilities. Typically, organizations strive to apply critical patches within 30 days of availability.
In the 2019 Kaseya State of IT Operations Survey results, about 65 percent of the participants responded that they apply critical OS patches within 30 days of release, about the same as the 68 percent that said they did so in 2018. This suggests the other 35 percent have either overlooked patches or it takes them longer than 30 days, leaving themselves exposed to cyberattacks.
Patching of third- party applications is even more of a concern. Only 42 percent of the survey participants monitor third-party software and apply critical patches for these within 30 days, similar to the 43 percent that said they did so in 2018.
Every software vendor has its own schedule of patch releases. Keeping up with patch releases across all of your vendors and deploying them on time can be a challenge for IT professionals. Therefore, automating the entire process of patch management can not only save time and effort of your IT team, but also ensure that every critical vulnerability is patched on time, keeping your systems secure.
So, have the SMBs automated their patch management process? Less than half have done so, according to the survey.
Automated patch management has not yet become a standard operating procedure for the majority of small and midsize companies. Only about 42 percent automate or plan to automate patch management.
Improving IT security is the topmost priority for most SMBs and automating the patch management process could help them stay ahead of the onslaught of cyberattacks. With cyberattacks having become the norm these days, maintaining up to date patches is critical to the business.
Would you like to know more about the state of IT operations of SMBs? Download the complete copy of 2019 Kaseya State of IT Operations Report for SMBs now.





